Signature Management & Analysis
Principles and Doctrine of Signature Management
In an era where technological advancements have democratized access to surveillance and targeting capabilities, signature management has emerged as a cornerstone of modern operational doctrine. Effectively managing and manipulating your observable signatures across all domains—physical, electromagnetic, thermal, and digital—is critical to maintaining survivability and achieving tactical advantage. At Last Frontier Defense Systems, we help organizations and operators understand, implement, and leverage signature management principles to mitigate detection and counter modern threats.
What is Signature Management?
Signature management is the deliberate practice of minimizing, masking, or manipulating observable indicators that adversaries use to detect, locate, or target friendly forces. These indicators, referred to as signatures, include but are not limited to:
Visual Signatures: Physical presence or movements that can be detected visually.
Thermal Signatures: Heat emissions from personnel, vehicles, or equipment.
Electromagnetic (EM) Signatures: Emissions from radios, sensors, and other systems operating in the electromagnetic spectrum.
Acoustic Signatures: Noise generated by movement, engines, or other mechanical systems.
Digital Signatures: Data emissions, such as those from mobile devices or network systems.
The Principles of Signature Management
1. Reduction
Minimize observable emissions or indicators through technological, procedural, and physical means. Examples include:
Camouflage and Concealment: Using natural or artificial materials to obscure visibility.
Power Management: Reducing transmission power on radios or limiting signal duration.
Low-Probability of Detection/Interception (LPD/LPI): Employing communication tools that avoid or minimize detection.
2. Masking
Hide friendly signatures within the natural environment or among other background emissions. Masking includes:
Utilizing terrain, vegetation, or urban infrastructure to blend visual and thermal signatures.
Operating within existing electromagnetic noise to mask EM emissions.
Overlapping movements with civilian or environmental patterns to obscure intentions.
3. Manipulation
Deliberately create or alter signatures to deceive and mislead adversaries about location, capabilities, or intentions. Techniques include:
Tactical Deception: Deploying decoys or false emitters to misdirect enemy targeting efforts.
False Emissions: Generating spoofed signals to simulate friendly or enemy movements.
Feints and Ruses: Conducting misleading maneuvers to manipulate adversary decision cycles.
4. Monitoring and Analysis
Effective signature management requires continuous monitoring and assessment of one’s own signatures. Operators should:
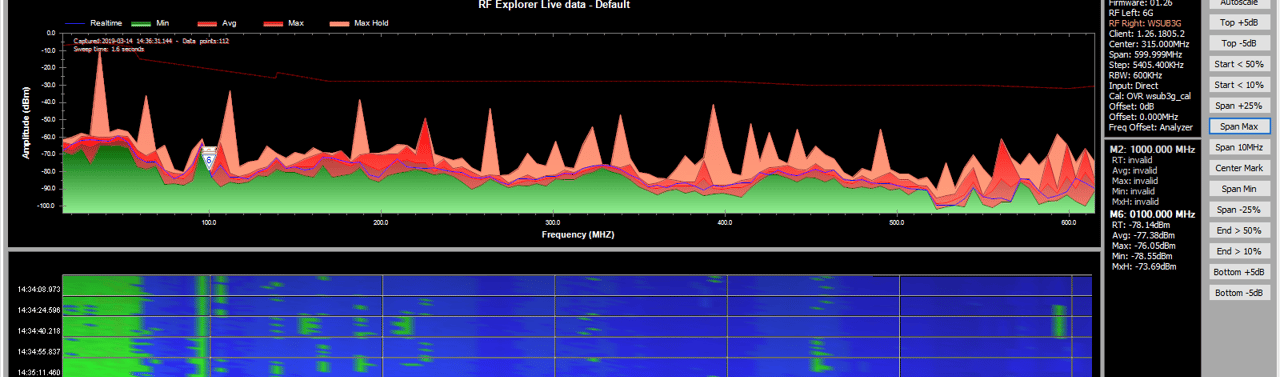
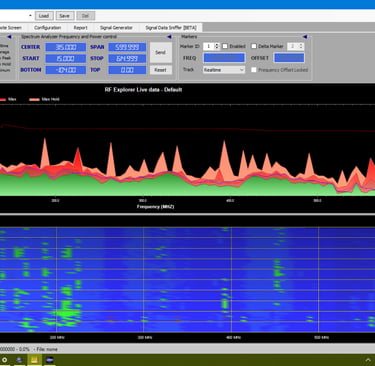
Conduct spectrum analysis to identify and mitigate unwanted EM emissions.
Employ tools like thermal and visual sensors to assess friendly detectability.
Perform adversary kill chain analysis to understand how your forces may be targeted.
5. Training and Discipline
Signature management is not simply a technology-driven solution—it demands deliberate training and discipline at every level of operation:
Educating teams on how their actions contribute to observable signatures.
Training operators to adhere to emissions control (EMCON) conditions.
Integrating signature management practices into planning, rehearsals, and after-action reviews (AARs).
Why Signature Management Matters
In modern conflict environments, adversaries ranging from peer competitors to irregular forces increasingly rely on advanced surveillance and targeting capabilities. Signature management provides:
Survivability: Reduces the likelihood of detection, thereby protecting personnel, equipment, and critical infrastructure.
Operational Security: Prevents adversaries from gathering intelligence about movements, posture, or intent.
Tactical Advantage: Enables forces to maneuver undetected while creating confusion for the adversary.
Implementing Signature Management
At Last Frontier Defense Systems, we offer tailored solutions to help you incorporate signature management principles into your operational planning and execution. Our expertise includes:
Signature Analysis and Assessments: Identifying vulnerabilities across all signature domains.
Training Programs: Educating operators on signature reduction, masking, and manipulation techniques.
Technological Integration: Providing systems for EM spectrum analysis, decoy deployment, and signature monitoring.
Moving Forward: Gain and Maintain the Tactical Edge
In an environment where detection equals destruction, signature management is not optional—it is essential. Through deliberate planning, advanced tools, and disciplined training, organizations can mitigate threats, protect assets, and maintain freedom of action across all domains.
Last Frontier Defense Systems
Giving you a chance to make a last stand in a new frontier.
Contact
admin@lastfrontierdefense.com
858-210-1049
© 2024. All rights reserved.
